Cybersecurity remains a major concern for many organizations as we move into a digital world. In 2022, data breach costs reached $4.35 million, increasing from $4.24 million in 2021. In this era, understanding how to secure cloud, on-prem, and hybrid infrastructure and coping with compliance burdens has become more crucial than ever before.
In the first half of 2022, over 53 million individuals were affected by data compromises, including data breaches, leakage, and exposure. As the digital threat landscape increases, it becomes critical to have effective cybersecurity controls in place. However, it is difficult for organizations to implement security controls without using any benchmark. Therefore, a security framework like the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) can help organizations implement implicit security controls.
This article will discuss the NIST framework and how organizations can implement it to enhance their cybersecurity posture.
What is the NIST Cybersecurity Framework?
NIST CSF is a comprehensive set of guidelines designed to help critical infrastructure owners and operators manage and reduce cybersecurity risks. The framework is voluntary. Nonetheless, its flexibility, common lexicon, and emphasis on using business drivers to shape cybersecurity initiatives have fueled the framework’s widespread appeal, adoption, and recognition as a requirement across all sectors and industries not only in the U.S. but also in numerous countries globally.
Importance of NIST Cybersecurity Framework?
NIST CSF is necessary for your organization for several reasons. It not only enhances your cybersecurity controls but also changes your organization’s security into a more responsive and adaptive one for managing cyber risks. NIST framework provides a strong strategy for continuous compliance that also is supported by the response and recovers functions.
Some benefits of this framework include:
- Enables effortless compliance
- Enables cybersecurity and integrated risk management
- Flexible and adaptable
- Unbiased and superior cybersecurity controls
How does the NIST Cybersecurity Framework Help Implement Security?
The five NIST CSF core functions and their corresponding categories provide a clear roadmap for businesses to implement cybersecurity strategies in their enterprise.
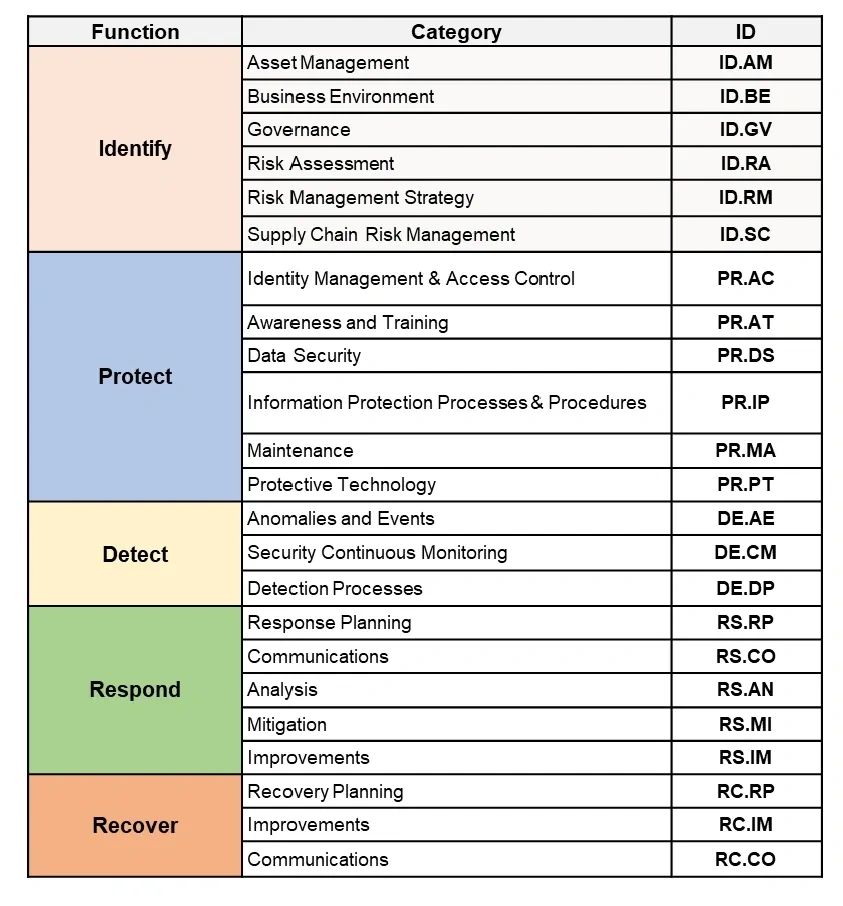
The five core functions of NIST CSF
Function 1: Identify (ID)
The Identify function entails understanding the organization and its operational context, assets, resources, capabilities, and risks so that cybersecurity efforts can be focused on and prioritized by existing risk management and organizational objectives. Its categories include:
- Asset Management: Identify and manage the data, personnel, devices, systems, and facilities that enable the organization to achieve business purposes with their relative importance to organizational objectives and the organization’s risk strategy.
- Governance: Understand the policies, procedures, and processes to manage and monitor the organization’s regulatory, legal, risk, environmental, and operational requirements.
- Risk Management Strategy: Establish the organization’s priorities, constraints, risk tolerances, and assumptions and use them to support operational risk decisions.
- Supply Chain Management: Establish and implement the processes to identify, assess and manage supply chain risks.
Function 2: Protect (PR)
The Protect function is about developing and implementing appropriate safeguards to ensure the delivery of critical services. This function supports the ability to limit and/or contain the impact of a potential cybersecurity event. This function entails the following categories.
- Identity Management and Access Control: Limit the access to physical and logical assets and associated facilities to authorized users, processes, and devices, and manage consistently with the assessed risk of unauthorized access to authorized activities and transactions.
- Awareness and Training: Provide cybersecurity awareness education to the organization’s personnel and partners and train them to perform their cybersecurity-related duties and responsibilities consistent with related policies, procedures, and agreements.
- Protective Technology: Manage technical security solutions to ensure the security and resilience of systems and assets, consistent with related policies, procedures, and agreements.
- Data Security: Manage information and records (data) consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information.
Function 3: Detect (DE)
The Detect function encompasses developing and implementing appropriate activities and controls to enable the timely and accurate discovery of a cybersecurity event. Its corresponding categories are given below.
- Anomalies and Events: Detect anomalous activity, and understand the potential impact of events.
- Security Continuous Monitoring: Monitor the network to detect potential cybersecurity events.
- Detection Processes: Maintain and test detection processes and procedures to ensure awareness of anomalous events.
Function 4: Respond (RS)
The Respond function is about developing and implementing suitable activities to act in response to a detected cybersecurity incident. This function supports the ability to contain the impact of such an incident. Its categories include:
- Response Planning: Execute and maintain response processes and procedures to ensure a response to detected cybersecurity incidents.
- Communications: Coordinate response activities with internal and external stakeholders (e.g., external support from law enforcement agencies).
- Analysis: Conduct analysis to ensure effective response and support recovery activities.
- Mitigation: Perform activities to prevent the expansion of an event, mitigate its effects, and resolve the incident.
- Improvements: Improve organizational response activities by incorporating lessons learned from current and previous detection/response activities.
Function 5: Recover
The Recover function is about developing and implementing activities to maintain plans for resilience and restore capabilities that were impaired due to a cybersecurity incident. It supports timely recovery to normal operations to reduce the impact of such an incident. It entails the following corresponding categories.
- Recovery Planning: Execute and maintain recovery processes and procedures to ensure the restoration of systems or assets affected by cybersecurity incidents.
- Improvements: Improve recovery planning and processes by incorporating lessons learned into future activities
- Communications: Coordinate restoration activities with internal and external parties (e.g., coordinating centers, Internet Service Providers, owners of attacking systems, victims, other CSIRTs, and vendors).
Enhance Your Cybersecurity Posture with Novesh!
An effective cybersecurity posture is critical to implicitly managing cybersecurity-related concerns. While NIST CSF is sufficient for any organization to enhance its cybersecurity controls, a security vendor like Novesh can help you strengthen your security with its best-in-class cybersecurity products and services.
Our cybersecurity risk assessments, architecture designing, and threat monitoring deliver secure network designing, continuous threat detection, and protection for industrial networks. We provide a unified security platform for the security of your on-prem, cloud, or hybrid IT infrastructure.
Streamline cybersecurity with Novesh Cybersecurity Solutions. Contact us to get a free consultation call today!