Industrial production activities are now monitored, managed, and run more effectively thanks to developments of advanced automation and control technologies. However, introducing new technological advancements and features can increase the attack surfaces in industrial automation and control systems (IACS) and critical infrastructure. Hence, it is crucially important to consistently evaluate these systems and their changes over time by following security standards and implementing their guidelines.
11% of survey respondents expect an increase in nation state-sponsored attacks on critical infrastructure. ~ Statista Companies' Threat Outlook 2023
To prevent data breaches and cyberattacks on IACS systems, compliance with IEC 62443 is essential. If an attack succeeds, unreliable parties could acquire confidential information, damage or shut down the entire network, and even bring down control systems.
The article discusses IEC 62443 and explains the compliance requirements of IEC 62443 that you need to know to ensure protected operations.
What is IEC 62443?
The IEC 62443 standards offer an all-encompassing and comprehensive method for protecting industrial automation systems. The International Electrotechnical Commission (IEC) 62443 is a collection of information security standards for commercial IACS.
The IEC 62443 standard helps to identify and address security weaknesses in IACS. Its objective is to minimize the risk of threats and failures in industrial control system (ICS) networks.
Breakdown of the IEC 62443 standards
This standard is made up of 13 separate documents that are divided into four categories: 1) General, 2) Policies & Procedures, 3) System, and 4) Component.
The first two groups of the IEC 62443 standard, General and Policies & Procedures, outline the key principles, use cases, and guidelines for securing industrial control systems. The latter two, System and Component, detail the technical specifications for ensuring the security of networks and their individual components.
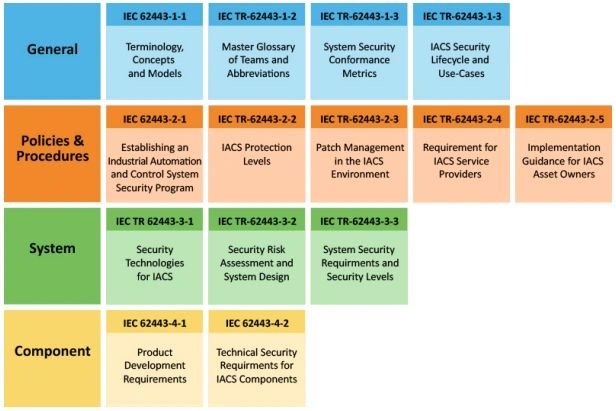
- General (62443-1): This group encompasses the fundamental concepts, definitions, and principles central to the entire series.
- Policies and Procedures (62443-2): This group includes the policies and procedures for IACS security, such as security program requirements for service providers, asset owners, and solution providers. It also presents a methodology for assessing the protection level of an operational IACS.
- System (62443-3): This category focuses on technical requirements and risk assessment processes for cyber security across the system.
- Component (62443-4): This group addresses the secure development lifecycle of system components and the technical security requirements of these components.
IEC 62443-3-3 and IEC 62443-4-2
The IEC 62443 series of standards provide different security requirements for the production of IACS/OT components as well as the operation of these systems in a network. These security control and requirements that have to be fulfilled by the system integrator and components manufacturers are given in IEC 62443-3-3 and IEC 62443-4-2 series of standards, respectively.
- IEC 62443-3-3: It outlines the general security requirements for systems, such as authentication measures, maintaining data confidentiality, and ensuring the system's integrity.
- IEC 62443-4-2: It lays out the technical specifications for ensuring the security of the various components that make up an IACS network.
Let's briefly discuss the fundamental requirements (FR) for these two IEC 62443 standards.
FR-1 Identification and Authentication Control
The IEC 62443-3-3 and IEC 62443-4-2 require that all human users accessing the control systems and components be authenticated for all applications and devices. Also, control systems and components shall prevent password reuse for a configurable number of generations and enforce lifetime restrictions for minimum and maximum passwords.
Furthermore, these standards discuss the requirements for monitoring and controlling all access methods to control systems or network devices through untrusted networks.
FR-2 Use Control
The standards IEC 62443-3-3 IEC 62443-4-2 requires that the control systems and components of IACS/OT systems shall have the ability to create audit records for various security categories, including access control, errors in requests, events related to the operating system and control system, backup and restore events, changes in configuration, indications of reconnaissance activity, and events related to audit logs.
FR-3 System Integrity
In order to maintain system integrity, the IEC 62443 standards require the integration of protection mechanisms for control systems and protection for malicious codes for network devices. Also, the control system and components must check the format and information of any input used for industrial process control or that directly affects the control system's actions.
Moreover, the control system and components should be able to identify and handle error conditions promptly for effective troubleshooting and remediation.
FR-4 Data Confidentiality
The standards require control systems and components to protect information confidentiality at rest as well as in transit. If, in case, control systems or components require cryptography, they must use cryptographic mechanisms according to security practices that are internationally recognized and proven.
FR-5 Restricted Data Flow
The IEC 62443-3-3 standard requires that control systems must have the ability to segment control system networks from non-control system networks as well as monitor the control communications at zone boundaries to implement the compartmentalization outlined in the risk-based zone and conduits model.
On the other hand, IEC 62443-4-2 requires support for segmented networks by components to support the broader network infrastructure based on logical segmentations. Also, it requires a network device at zero boundaries to monitor and control communications.
FR-6 Timely Response to Event
For timely response to events, the control systems and components must be able to provide authorized human and/or tool access to audit logs on a read-only basis. Also, control systems must be able to continuously monitor security mechanisms using commonly accepted industry practices and recommendations to detect, identify, and report breaches timely.
While the components should also be monitored continuously to detect, identify, and report security breaches.
FR-7 Resource Availability
In the event of a DDoS attack, the control system and components shall remain operative and maintain essential functions. Also, they must be able to restrict unnecessary usage of ports, functions, protocols, and/or services. In addition, the control system must report the current list of installed components, while the components must be able to support a control system for its inventory.
Simplifying IEC 62443 Compliance with Novesh
Adhering to these requirements of IEC 62443 can be difficult and time-consuming, but there are several actions that businesses can take to make the process easier.
Working with Novesh, a cyber security specialist, can help you make IEC 62443 compliance simpler. We ensure best practices and assist firms in locating and resolving potential ICS system vulnerabilities. Our team of experts can help you create and practice a thorough security plan that complies with IEC 62443 requirements.
Contact us to get your hands on world-class services to protect your business's confidential data and assets from cyber threats