Industrial Control Systems (ICS) are an integral part of modern industrial operations, used to monitor and control critical infrastructure such as power plants, water treatment facilities, transportation systems, and manufacturing plants. The reliance on ICS has increased significantly over the years, making them a prime target for cyber attackers.
In recent years, there have been several high-profile cyber attacks on ICS, resulting in significant disruption to critical infrastructure, and in some cases, physical damage. These attacks have highlighted the importance of securing ICS against cyber threats and the potential consequences of a successful attack on industrial control systems.
ICS cyber attacks can lead to the disruption of operations, the loss of sensitive data, and in some cases, physical harm to people and damage to equipment. The Stuxnet attack on Iran's nuclear facilities in 2010, for example, caused physical damage to the facility, while the Ukraine power grid attack in 2015 and 2016 caused widespread power outages and significant economic damage.
Securing ICS against cyber threats is critical to protecting critical infrastructure and ensuring public safety. This requires a multi-layered approach that includes regular risk assessments, security best practices, and advanced cybersecurity technologies. Compliance with the IEC 622443-3-2 standard can help businesses better assess cyber risk, reduce threat exposure, and minimize vulnerabilities. The article discusses the IEC 622443-3-2 standard and how OT sectors can follow this standard to minimize cyber threat exposure, which is a critical step toward improving the security posture of industrial control systems.
What is IEC 62443-3-2?
The IEC 62443-3-2 standard provides guidelines for assessing and managing cybersecurity risks in Industrial Automation and Control Systems (IACS). This standard introduces the concept of Zones and Conduits (ZC) for security risk assessment. Following the ZC model is an important step towards improving the security posture of ICS and minimizing vulnerabilities to cyberattacks.
Zones & Conduits Requirements (ZCR) in IEC 62443-3-2
Zones & Conduits Requirements (ZCR) is a key component of the IEC 62443-3-2 standard, which provides guidelines for implementing a security risk assessment process for industrial control systems (ICS). The ZCR guidelines focus on creating logical boundaries within the system under consideration (SuC), called "zones," and controlling the flow of information between assets within these zones, using "conduits." The ZCR process involves identifying the assets within the SuC, assessing their criticality and potential risks, and creating logical zones and conduits to protect critical assets and control the flow of information between them. The ZCR guidelines provide a framework for ensuring the security of ICS environments, including critical infrastructure systems, and are an essential part of an effective security risk management program.
- ZCR 1 - Identification of the System under Consideration (SuC)
- ZCR 2 - High-Level Cybersecurity Risk Assessment
- ZCR 3 - Partition the SuC into zones and conduits
- ZCR 4 - Risk Comparison
- ZCR 5 - Perform a detailed cybersecurity risk assessment
- ZCR 6 - Document cybersecurity requirements, assumptions, and constraints
- ZCR 7 – Asset Owner Approval
s serves a specific purpose in the security risk assessment process for industrial control systems (ICS), ranging from identifying the system under consideration to establishing a cybersecurity program for the IACS supply chain. By following these guidelines, ICS operators can create a secure and robust system that is better able to withstand cyber-attacks and other security threats. Below we provide a brief description of each requirement.
ZCR 1: Identification of the system under consideration (SuC)
IEC 62443-3-2's Zones & Conduits Requirements (ZCR) model ZCR 1 requirement outlines how to identify the system under consideration (SuC).
ZCR 1.1 Identify SUC perimeter and access point
ZCR 1.1 outlines the requirements to identify and record the System Under Consideration (SuC) and its boundaries. The SuC may consist of hardware, software, network, and human components. To ensure that the assessment process includes all pertinent components and that the results appropriately reflect the security posture of the system, it is crucial to define the SuC precisely. The process of establishing the parameters of the system to be evaluated is referred to as "identification of the system under consideration (SuC)". This phase of risk assessment process is necessary to make sure that every system component that is essential to the system's overall security posture is considered during the assessment process. The results of the ZCR 1 phase will provide the foundation for the subsequent phases of the security risk assessment process, including threat and vulnerability analysis, risk evaluation, and risk mitigation.
ZCR 2: High-level cyber security risk assessment
A high-level evaluation of the potential hazards to industrial control systems (ICSs) and process controls within an enterprise from cyber threats is referred to as a ZCR 2 High-Level Cyber Security Risk Assessment.
ZCR 2.1 Perform High-level Cyber Security Risk Assessment
ZCR 2.1 is the process of evaluating the overall security posture of the system under consideration (SuC) in order to identify and prioritize the most critical security risks. This phase builds on the information gathered during ZCR 1, and typically involves the following steps:
Threat and vulnerability analysis: This step involves identifying and analyzing the potential threats and vulnerabilities associated with the SuC, and determining the likelihood and impact of these threats and vulnerabilities.
Risk evaluation: This step involves combining the results of the threat and vulnerability analysis with an understanding of the critical assets and functions of the SuC to determine the overall risk level associated with each threat and vulnerability.
Risk prioritization: This step involves prioritizing the risks identified in the risk evaluation phase based on their impact and likelihood, and determining which risks need to be addressed first in order to improve the overall security posture of the SuC.
The results of the ZCR 2 phase provide a high-level understanding of the security risks associated with the SuC, and serve as the foundation for the subsequent phases of the security risk assessment process, including risk mitigation and ongoing risk management.
ZCR 3: Partition the SuC into zones and conduits
Splitting an industrial control system (ICS) into security zones and conduits is partitioning the SuC. Partitioning aims to establish a distinct division between various ICS components to manage potential security concerns more successfully.
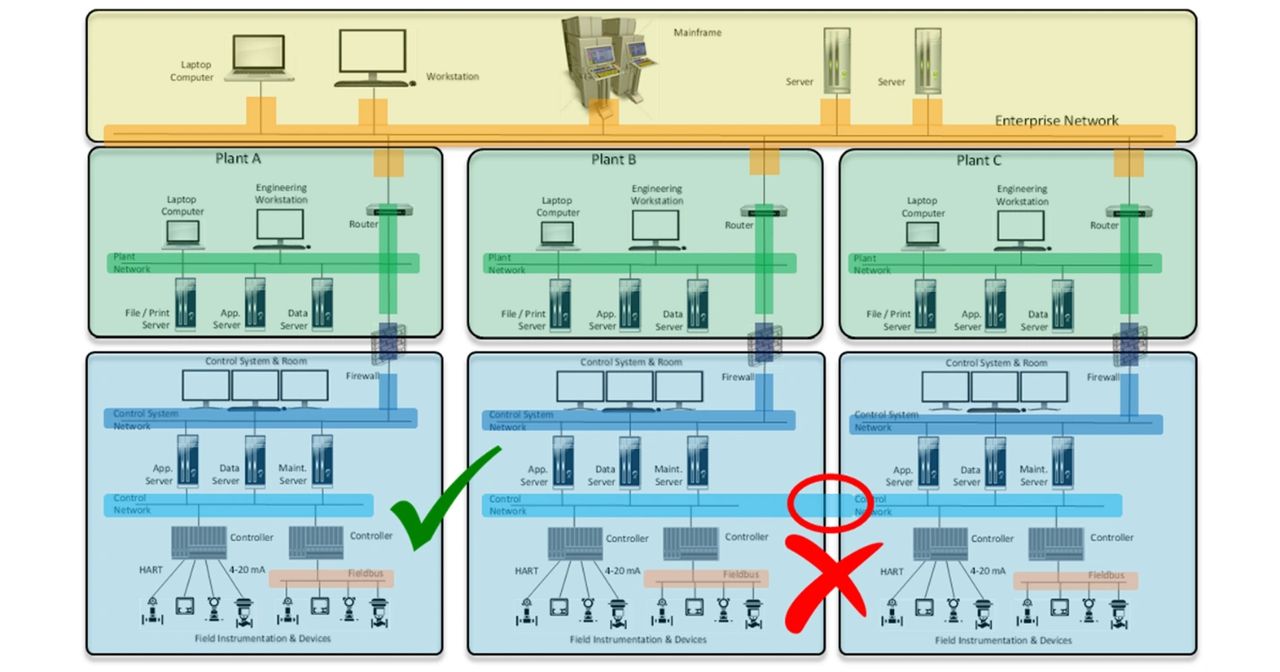
Example of Zone and Conduits Configuration, Provided by ISA Standard
ZCR 3.1: Establish Zone and Conduit
ZCR 3.1 describes the procedure for dividing an industrial control system (ICS) into conduits and security zones. The results of the ZCR 3.1 phase will be the creation of logical boundaries and paths within the SuC to control the flow of information between assets and provide the foundation for the ongoing risk management process, including the ongoing monitoring of the security posture of the SuC.
ZCR 3.2: Separate Business and IACS Assets
To protect vital infrastructure, it is crucial to separate business and industrial control system (IACS) assets. Organizations can lower the likelihood that a cyber assault has on their IACS or vice versa by isolating IACS and business assets. There might occasionally be a need for a little amount of communication between the two networks. To lessen the risk of a cyber attack in such circumstances, it is crucial to install rigorous security measures and to carefully monitor any access between the two networks.
ZCR 3.3: Separate Safety-Related Assets
ZCR 3.3 "Separation of safety and related assets" refers to the process of ensuring that safety and related assets are isolated from other assets in the system under consideration (SuC). This is to reduce the risk of harm to human life in the event of a security breach. The results of the ZCR 3.3 phase should result in the safe and effective separation of safety and related assets within the SuC.
ZCR 3.4: Separate Temporarily Connected Devices
The goal of ZCR 3.4 is to reduce the risk of cybersecurity incidents by isolating devices that are only connected to the system temporarily, such as laptops, USB drives, and other mobile devices. The rationale behind this ZCR is that temporary devices may be more vulnerable to cyber attacks than devices that are permanently connected to the system. By temporarily isolating these devices, it is possible to prevent them from introducing malware, viruses, or other cybersecurity threats to the system. ZCR 3.4 also includes guidelines for verifying the security posture of temporarily connected devices before they are allowed to connect to the system.
ZCR 3.5: Separate Wireless Devices
ZCR 3.5 provide guidelines to reduce the risk of cybersecurity incidents by isolating wireless devices from the main control system network. To implement ZCR 3.5, ICS operators should identify all wireless devices connected to the system and ensure that they are isolated from the main control system network. This can be achieved by creating a separate wireless network with its own security controls and firewalls. The wireless network should be regularly monitored for any signs of suspicious activity, and all wireless devices should be scanned for malware and viruses before they are allowed to connect to the network.
ZCR 3.6: Separate devices connected via external networks
ZCR 3.6 is focused on the process of separating devices connected via external networks. The purpose of ZCR 3.6 is to reduce the risk of cybersecurity incidents caused by unauthorized access to the system through external networks. This includes networks such as the internet, remote access networks, or networks used for software updates. The network separation should be regularly reviewed and updated to ensure that it is effective in limiting the flow of network traffic between the external networks and the main control system network.
ZCR 4 Risk Comparison
This part of the standard deals with the process of comparing the initial risk of the System under Consideration (SuC) to the tolerable risk levels established by the ICS operator.
ZCR 4.1 is Compare initial risk to tolerable risk
In this phase of risk assessment, the analyst determines whether the initial risk level is acceptable or if additional risk reduction measures need to be implemented to reduce the risk to an acceptable level. To implement ZCR 4.1, the ICS operator first needs to establish tolerable risk levels for the SuC. These levels are based on the criticality of the SuC, its impact on safety, security, and productivity, and any legal or regulatory requirements. Once the tolerable risk levels have been established, the initial risk levels are compared to these levels to determine if any additional risk reduction measures are necessary.
ZCR 5: Perform a detailed cybersecurity risk assessment
This requirement deals with performing a detailed cybersecurity risk assessment of SuC. The goal of this ZCR is to identify and analyze the specific cybersecurity risks facing the SuC and to determine the appropriate risk reduction measures to address these risks. To implement ZCR 5, a detailed cybersecurity risk assessment should be performed using a structured and systematic process. It consists of 13 subsections that guide the process of performing a detailed cybersecurity risk assessment. Here is a brief overview of each of the subsections:
- ZCR 5.1 Identify threats.
- ZCR 5.2 Identify vulnerabilities
- ZCR 5.3 Determine consequence and impact
- ZCR 5.4 Determine the unmitigated likelihood
- ZCR 5.5 Determine unmitigated cyber security risk
- ZCR 5.6 Determine the security level target (SL-T)
- ZCR 5.7 Compare unmitigated risk with tolerable risk
- ZCR 5.8 Identify and evaluate the existing countermeasures
- ZCR 5.9 Revaluate Likelihood and impact
- ZCR 5.10 Determine residual risk
- ZCR 5.11 Compare residual risk with tolerable risk
- ZCR 5.12 Identify additional cyber security countermeasures
- ZCR 5.13 Document and communicate the results
Each of these subsections is designed to provide guidance on different aspects of the risk assessment process, from identifying assets and threats to analyzing risk scenarios and evaluating the effectiveness of security controls. By following the guidelines set out in each subsection, the analyst can perform a thorough and effective cybersecurity risk assessment to provide a comprehensive understanding of the specific risks facing their SuC.
ZCR 6: Document cybersecurity requirements, assumptions, and constraints
In this phase of assessment, cybersecurity analysts document the cyber security requirements, assumptions, and constraints for the SuC. This involves capturing and organizing the output from the risk assessment process in a clear and actionable way, which provides a basis for implementing and maintaining effective cyber security controls. ZCR 6 consists of the following subsections:
- ZCR 6.1 Cyber security requirements specification
- ZCR 6.2 SUC description
- ZCR 6.3 Zone and conduit drawings
- ZCR 6.4 Zone and conduit characteristics
- ZCR 6.5 Operating environment assumptions
- ZCR 6.6 Threat environment
- ZCR 6.7 Organizational security policies
- ZCR 6.8 Tolerable risk
- ZCR 6.9 Regulatory requirements
By documenting these requirements, the analyst can provide a clear and concise set of guidelines for designing, implementing, and maintaining effective cybersecurity controls that protect the SuC against the specific risks identified in the risk assessment.
ZCR 7 Asset owner approval
ZCR 7 in IEC 62443-3-2 requires that the cybersecurity measures put in place for the system under consideration (SuC) are reviewed and approved by the asset owner. The asset owner is the individual or organization that owns the SuC and is responsible for ensuring that it is secure.
Using this requirement, the analyst ensures that the asset owner is aware of the cybersecurity measures that are being put in place, and that they have the opportunity to review and approve these measures before they are implemented. This helps to ensure that the cybersecurity measures are appropriate for the SuC, and that they meet the requirements of the asset owner.
Enhance Your ICS’ Security Posture with Novesh
Implementing IEC 62443-3-2 Zones, Conduits, and Risk Assessment standards to improve business operations while enhancing maximum security can be daunting without professional help.
On that note, Novesh offers the best IT & OT cybersecurity services using top-notch technology to ensure you never have to worry about your business data confidentiality and breaches. To better safeguard your industrial control system, reach out to our professionals to implement IEC 62443-3-2 zones and conduits to ensure maximum protection.
Contact us to join hands with the world-leading cybersecurity service providers to protect assets from cyber threats and safeguard your business data.